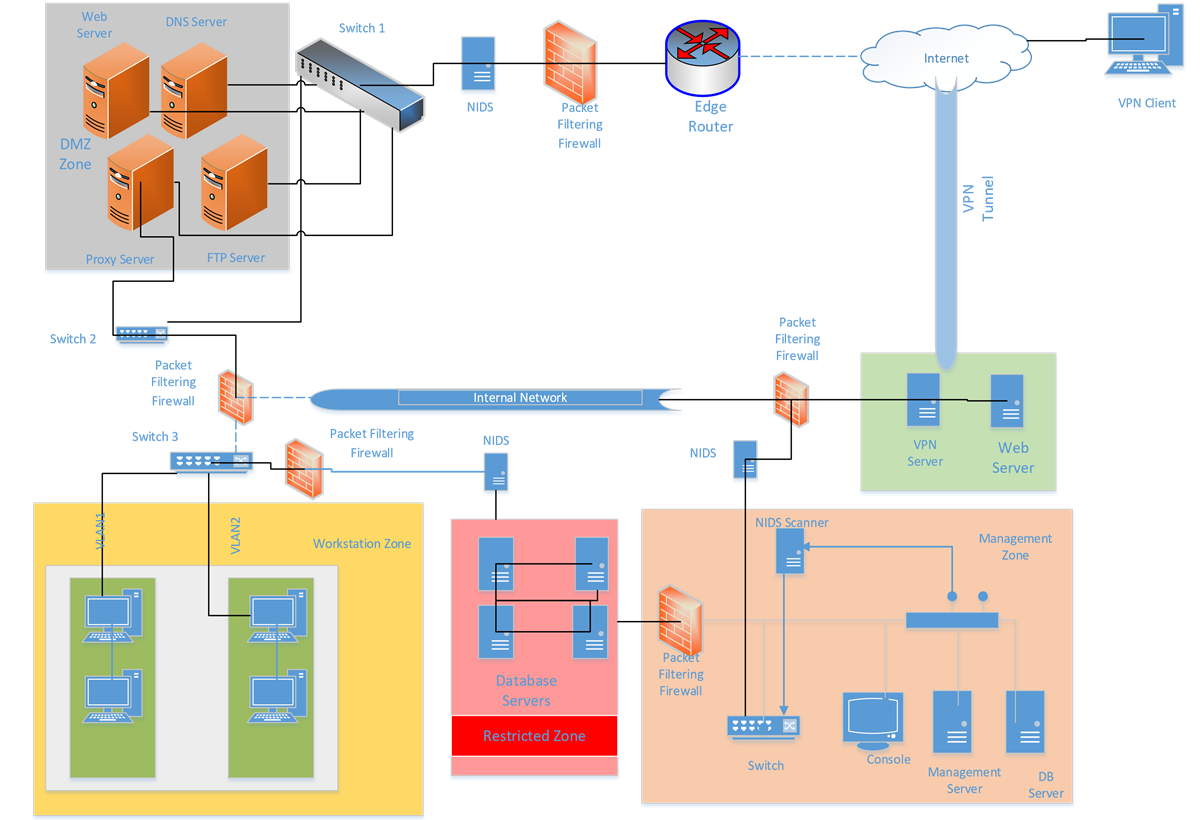
42 network security architecture diagram
July 18, 2021 - A consolidated cyber security architecture protects an organization’s entire IT infrastructure across networks, cloud, IoT, endpoint and mobile.
September 15, 2020 - Network diagrams form the blueprints for security programs in the 21st Century. Unfortunately, creating and maintaining these network architecture diagrams has become the IT equivalent to bookkeeping – it’s a…
Network Diagram Software LAN Network Diagrams & Diagrams for LAN Physical Office Network Diagrams Local area network connects computers and other network appliances within an area, such as office building or a campus. It can be difficult to provide such network without a predesigned plan. The Best Free Network Monitoring Tools.

Network security architecture diagram
[Audacity](http://www.audacityteam.org/) is an intuitive open-source multi-track audio editor and recorder. mythofechelon tells us, "I'm hardly an audiophile and definitely not an audio engineer, but any changes that I've ever needed to make to an audio file (convert from FLAC to 320 KbPS MP3, add fades, splice tracks, etc.) has been easily handled by Audacity, especially when you add additional libraries (LAME for MP3, FFmpeg, etc.)" [Bees With Machine Guns](https://github.com/newsapps/beeswit...
Apr 30, 2016 - The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share ...
The following diagram provides an overview of the solution architecture: Application and Data Flow The application architecture is organized through a set of independently operable microservices.
Network security architecture diagram.
A network security diagram maps out the security methods implemented to protect an organization's assets. It helps to ensure the protection of valuable information as it is stored and transmitted. Make sure your data is safe by using this network security diagram template for your organization.
Disclaimer, this is a fanfic only, all credit belongs to [u/BlueFishcake](https://www.reddit.com/u/BlueFishcake) alone. I hope to keep this train wreck of a story going cos I know I enjoy writing it, also I’m hoping that some bits of this story becomes official lore :) - I’d like to thank the legend known as [u/HellowShel](https://www.reddit.com/user/HollowShel/) for given this train wreck the once over, and making my shity writing more readable, and another thank you to [u/MajnaBunny](https://...
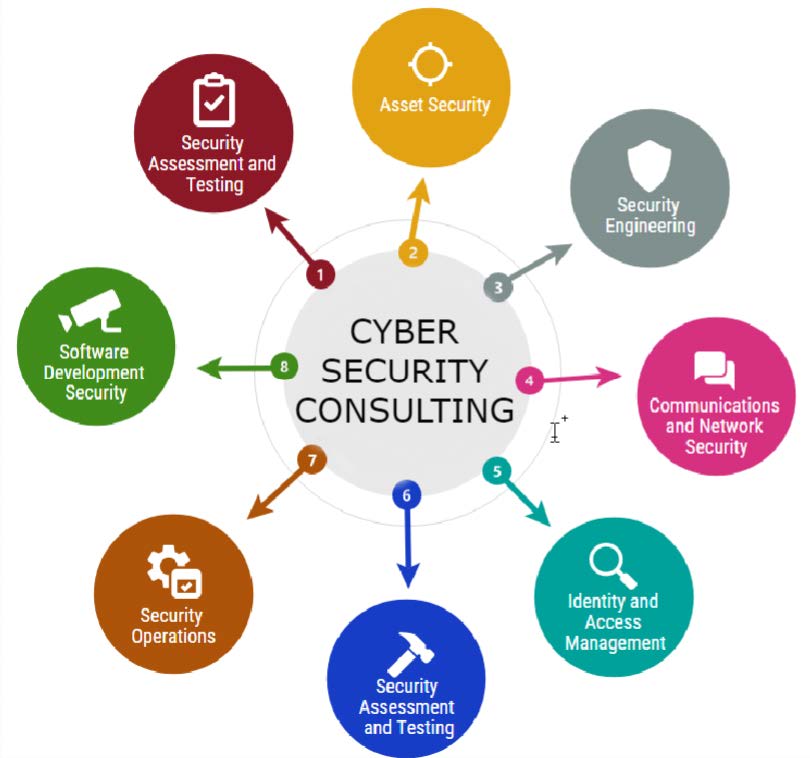
August 23, 2021 - Guide to Security Architecture. Here we also discuss the introduction and components of security architecture along with benefits.
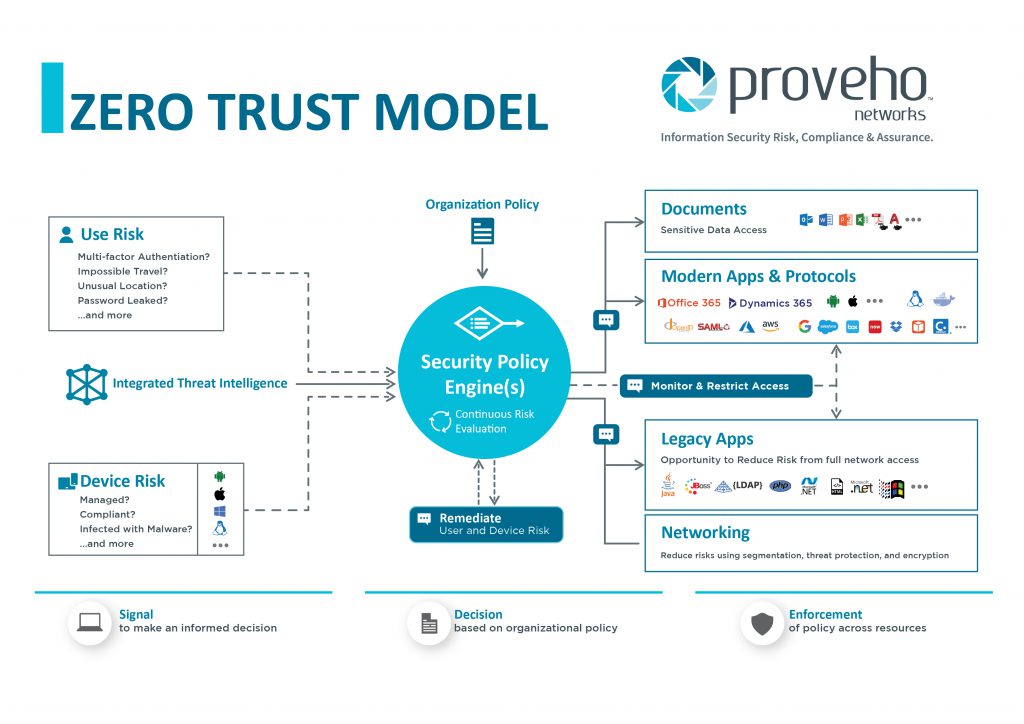
Use the following design considerations for this architecture: By default, OCI uses a zero-trust security model. With zero-trust security, no one is trusted by default from inside or outside the network. Security lists control network ingress traffic to the VCN, network traffic from within the VCN, and between subnets.
UI events are actions that should be handled in the UI layer, either by the UI or by the ViewModel. The most common type of events are user events. The user produces user events by interacting with the app—for example, by tapping the screen or by generating gestures. The UI then consumes these events using callbacks such as onClick () listeners.
Hello! I started OMSCS in Spring 2019 and just wrapped up this semester. My academic background was chemical engineering from a large state school, and my professional background was/is in consulting for a cloud provider. I took this program for the credentials, and for a deeper understanding of some of the "why" concepts that I deal with at work. Here are the classes I took and my personal review and stack ranking of each class. **Graduate Intro to Operating Systems (Spring 2019)** Th...
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to ...
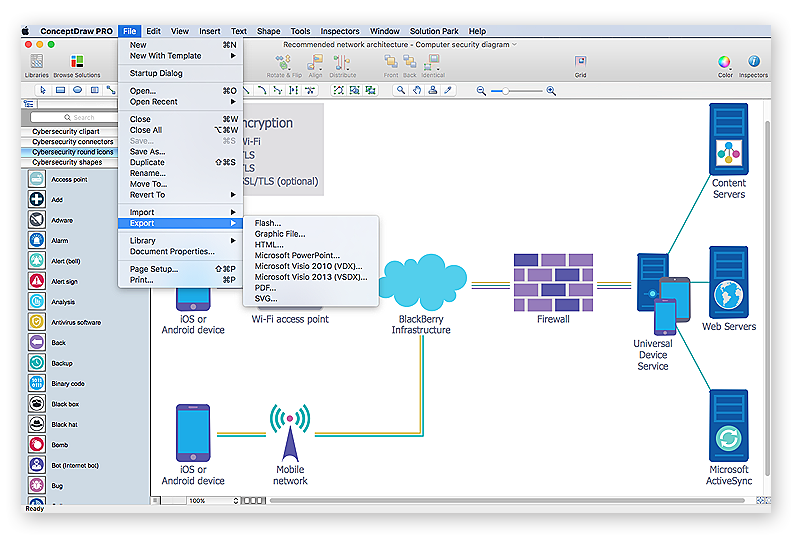
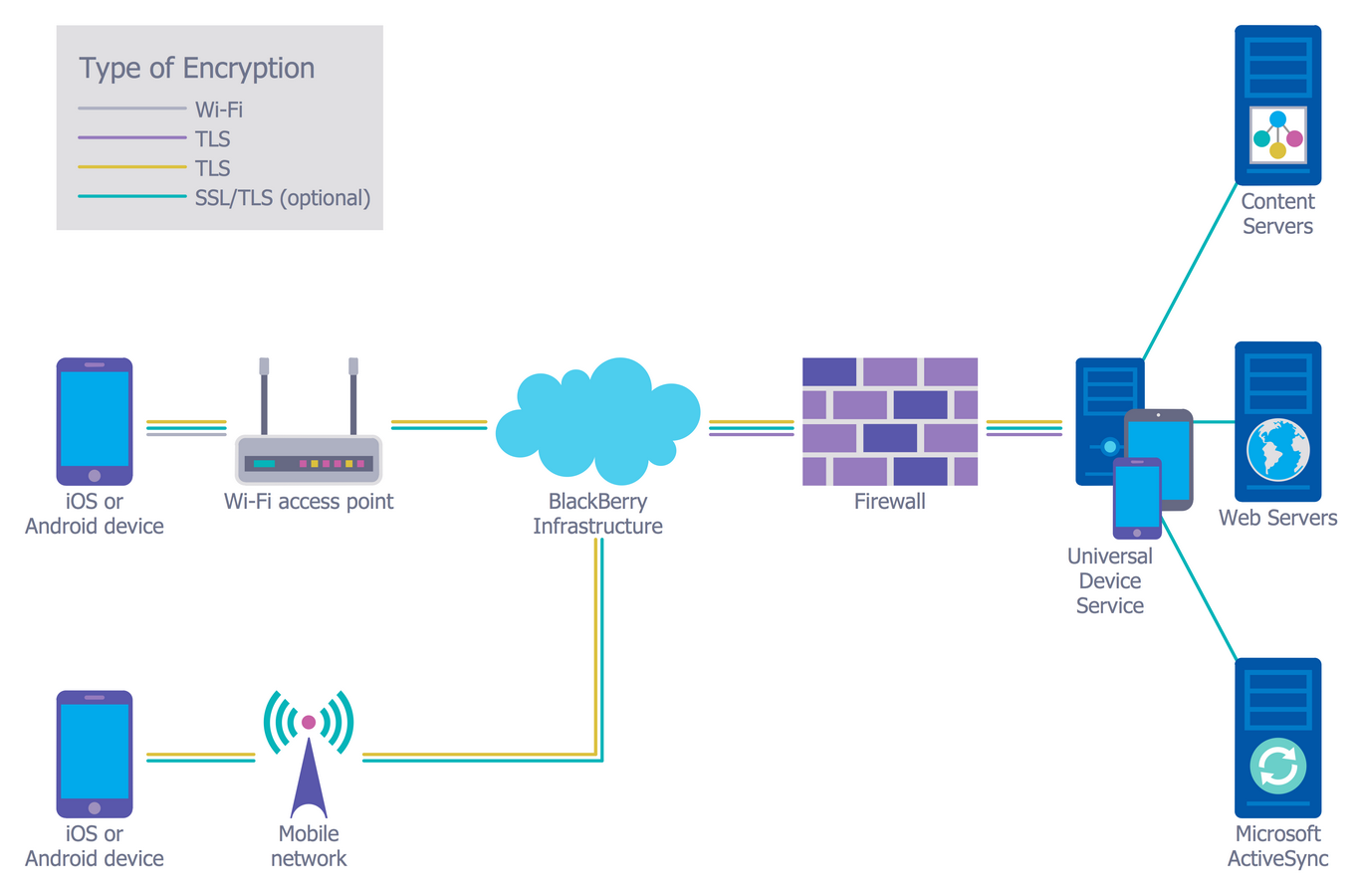
Example 4: Recommended Network Architecture. This diagram was created in #ConceptDraw PRO using the libraries from the #Network #Security #Diagrams Solution. This sample is an excellent example of network architecture with marked on it the types of cryptographic protocols.
Winter Park Library & Events Center. It's been humbling and inspiring to work together with the City of Winter Park and the many local champions of this project to realize this 21st century prototype of a multi-purpose knowledge campus in the public realm. As a centerpiece of the revitalized MLK Jr. Park, the new campus is designed as a ...
08.02.2021 · Creately let you draw a flowchart, organizational chart, wireframe, network diagram, infographics, and much more. It’s a complete drag-n-drop, so creating an infrastructure diagram or flowchart is easy. Coggle. Work together with your team to create a flowchart and mind maps using Coggle. Some of the features are as follows.
Network Architecture Diagrams. UML standard has no separate kind of diagrams to describe network architecture and provides no specific elements related to the networking.Deployment diagrams could be used for this purpose usually with some extra networking stereotypes.Network architecture diagram will usually show networking nodes and communication paths between …
• Should be proficient in Business knowledge, Business Change Management, Functional Architecture Design & Project Financials, KPI´s & Reporting. • Should have progressing skills on Software Engineering & Architecture Knowledge. • Should have baseline in Testing.
Example 4: Recommended Network Architecture. This diagram was created in ConceptDraw DIAGRAM using the libraries from the Network Security Diagrams Solution. An ...
TCSS 576 Wireless and System Security (5) Covers fundamental concepts in wireless network security and computer system security. Exposes the students to cutting-edge research results and hands-on experiences in cybersecurity. Topics include but are not limited to: 802.11 standard and its security, and system security evaluation. Prerequisite ...
Network Security Architecture Diagram. Network security is the set of actions adopted for prevention and monitoring the unauthorized access, ensuring information security and defense from the attacks, protection from misuses and modification of a network and its resources.. Network Security Architecture Diagram visually reflects the network's structure and …
* **If you find your book in the thread below, send the number of the book via** **reddit chat or via** [**telegram**](https://t.me/textbooks4cheap) **.** * **Almost all the books are in their latest editions and some of them are available in multiple editions too** * **Books (pdf) are delivered through Google-Drive link** * **You can also send requests via reddit chat or by** [**telegram**](https://t.me/textbooks4cheap) **.** * **Also, upvote the post if you found it useful** Please find the l...
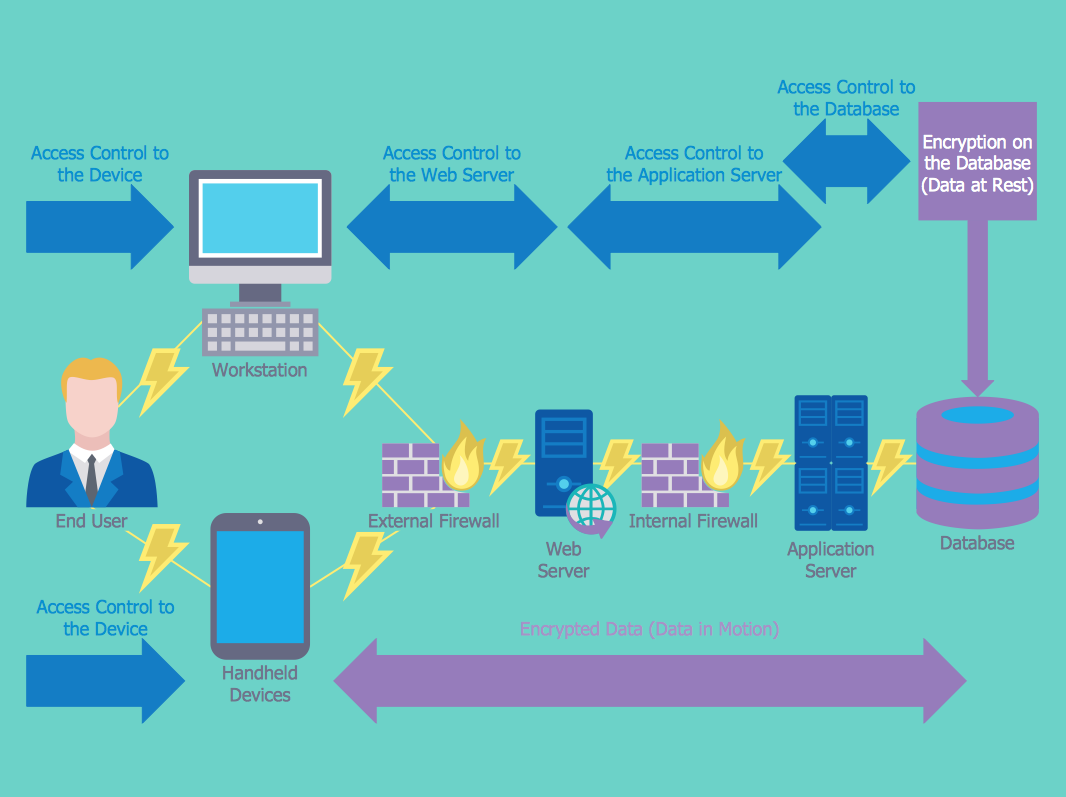
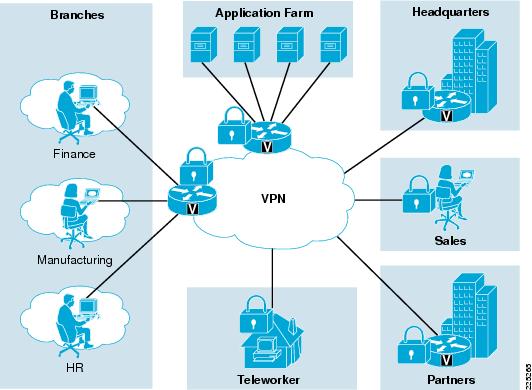
A network diagram can be either physical or logical. Logical network diagrams. A logical network diagram describes the way information flows through a network. Therefore, logical network diagrams typically show subnets (including VLAN IDs, masks, and addresses), network devices like routers and firewalls, and routing protocols.
The Autodesk Security Team is investigating the Log4Shell vulnerability (CVE-2021-044228). We have not identified any compromised systems in the Autodesk environment due to this vulnerability at this time. This is an ongoing investigation and we will provide updates on the Autodesk Trust Center as we learn more.
April 28, 2020 - Without strong security, your organization can be left vulnerable to a number of threats. Read on to learn about the purpose of cybersecurity architecture.
This course teaches the security mindset and introduces the principles and practices of computer security as applied to software, host systems, and networks. It covers the foundations of building, using, and managing secure systems. Topics include standard cryptographic functions and protocols, ...
September 23, 2020 - Our team of experts and analysts ... their security and efficiency — especially in the event of contingencies, problems and emergencies. Our goal is to ensure that your IT resources and investments will be put to maximum use by giving you the best network architecture diagram that aligns ...
Many applications perform scheduled tasks. For instance, you might want to automatically publish an article at a given time, change prices for offers which were defined weeks in advance, or notify customers 8 hours before a flight. These might be one-off tasks, or recurring ones. On Unix-like operating systems, you might have opted for the […]
I just passed C726. It took me close to a week to complete Task 1 and then the following day I powered through Task 2 in an 11 hour session. All of this was only possible due to this subreddit. I’m posting this because r/WGU got me through this class, and I hope to contribute something that might help someone else in turn. Below are things I wish I knew from the outset and answers to questions I had as I was working. But before I begin, I’d first like to shout out a few posts and resources ...
This family defines architectural models, governance, and transition initiatives to coordinate stakeholders and enable business change, with consideration of application, information, technology and security architecture. Qualifications. Bachelors and Advanced Degree in related field or equivalent work experience
This is undoubtedly a stupid question to some (or many?), so sorry in advance. The reason I say this is a stupid question is because I feel like it is asking a lot of different things and is vague in some regards. All of the security certification materials I come across do a good job of explaining things in their own little silos. Here's how IDS works, here's how a WAF works, here's how storage works, etc. I can't seem to find anything that shows how everything ties together. I don't know how ...
ConceptDraw DIAGRAM provides the toolkit for network security system visualization with its Network Security Diagram solution. Secure Network Architecture ...
A network diagram shows how computers and network devices (e.g. router, switch, etc) connect with each other within a network. It is widely used in network architecture design. A typical use of network diagram is for tracking down network issues by studying how the computers and devices are connected and inter-related.
[Audacity](http://www.audacityteam.org/) is an intuitive open-source multi-track audio editor and recorder. mythofechelon tells us, "I'm hardly an audiophile and definitely not an audio engineer, but any changes that I've ever needed to make to an audio file (convert from FLAC to 320 KbPS MP3, add fades, splice tracks, etc.) has been easily handled by Audacity, especially when you add additional libraries (LAME for MP3, FFmpeg, etc.)" [Bees With Machine Guns](https://github.com/newsapps/beeswit...
CSS 432 Network Design and Programming (5) QSR Examines OSI architecture, TCP/IP protocols, data link networks, packet switching, routing, routing protocols, security, performance evaluation, flow control, and congestion control. Networks are explored in the context of protocol development, implementation, writing of functionality, and inter ...
This basic network security template can help you: - Visualize the components of a basic network. - Understand the flow of information and interactions among network devices. - Design your own network diagram. Open this template to view a basic network security diagram example that you can ...
# Overall Writeup of Classes Taken While at WGU LONG post incoming.... DISCLAIMER: Some of the classes I will write about will change and have changed from when I've taken them (in fact one class I initially started is no longer offered in the Comp Sci program). WGU regularly updates classes, resources, PAs/OAs, etc... so this will only reflect my experience with the classes and how I felt about the classes looking back on them not to mention "difficulty" is an entirely arbitrary rating based...
* **Kindly note that the price range mentioned above is only for the books in the megathread list. Any requested books unavailable in the list can cost more, so please do not make any wrong assumptions.** * **If you find your book in the thread below, comment "PMed" below and then send your request by clicking [here](https://www.reddit.com/message/compose?to=bookseller10&subject=eBook/eTextbook+request) (expect super quick replies).** * **Don't mention the title of the book in comments sec...
The Autodesk Security Team is investigating the Log4Shell vulnerability (CVE-2021-44228) and (CVE-2021-45046). We have not identified any compromised systems in the Autodesk environment due to this vulnerability at this time. This is an ongoing investigation and we will provide updates on the Autodesk Trust Center as we learn more.
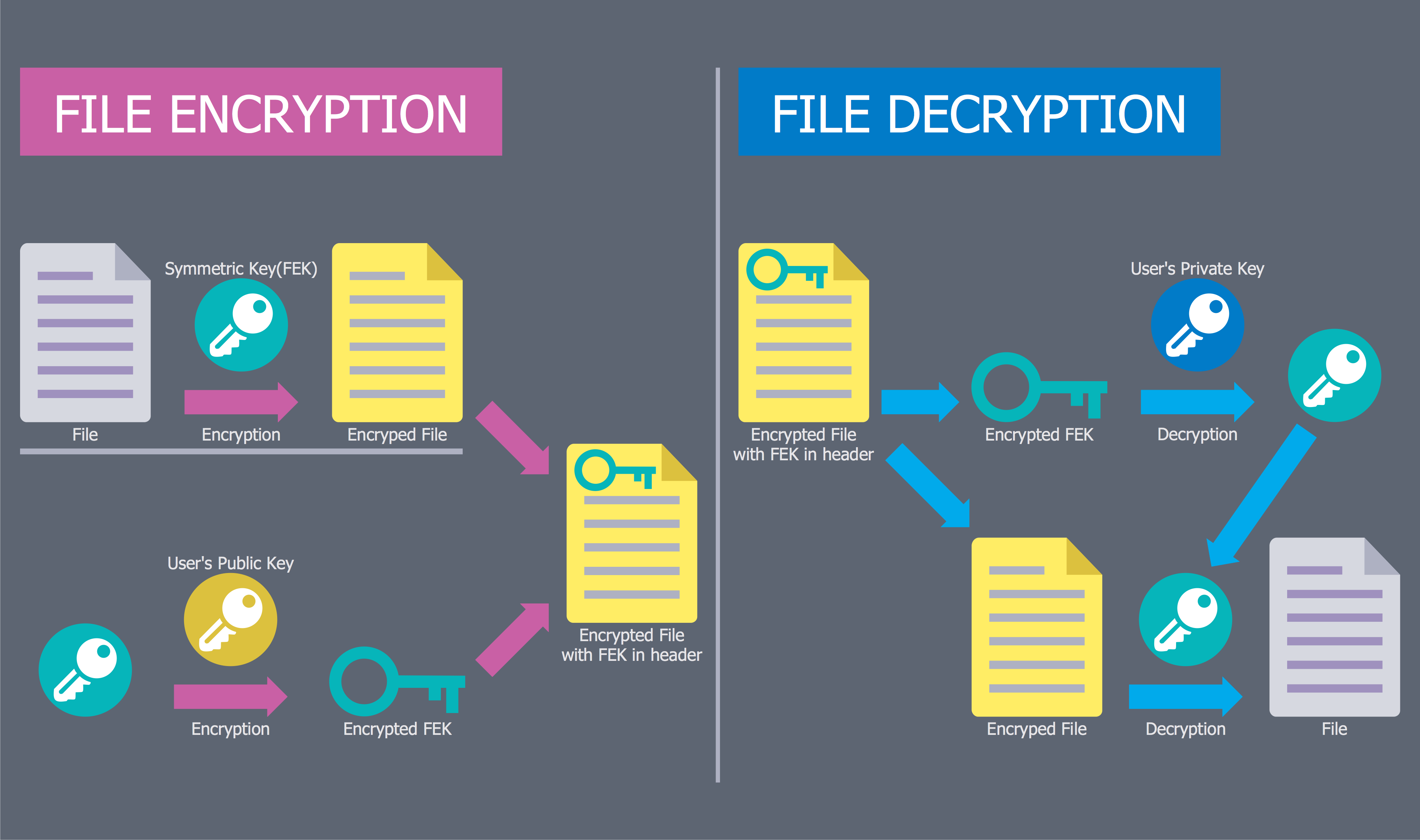
Codes and ciphers run any blockchain technology, even emails, online shopping, and entertainment. Cryptography is the name of the game, where it allows communications through channels and serves as protection for information. With the escalation of cyber attacks, there is a need in protecting data and intellectual property. That is cryptography and encryption. After all, encryption is necessary. The only thing we should look after is technology and services. Now, let's take a look and evaluate...
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network ...
The goal of the Site Reliability Engineer (SRE) Nanodegree program is to equip software developers with the engineering and operational skills required to build automation tools and responses that ensure designed solutions respond to non-functional requirements such as availability, performance, security, and maintainability. The content will focus on both designing systems to automate ...
SAST - Looking for coding and design conditions indicative of security vulnerabilities, these tools analyze application source code, byte code, and binaries in a non-running (static) state. To locate application layer vulnerabilities, SAST tools detect the source function - the "entry point" where user input is entered - and the sink function (e.g., database call, system call) that ...
Mitigating the log4j Vulnerability (CVE-2021-44228) with NGINX. security, ModSecurity web application firewall (WAF), NGINX App Protect WAF, CVE-2021-44228. Friday, December 10, 2021 is a date that will be remembered by many IT folks around the globe. It's when a highly critical zero‑day vulnerability was found in the very popular logging ...
Zero trust is about increasing your use of identity as a means to grant access in addition to traditional controls that rely on network being private. Apply "defense in depth" to your application infrastructure with a layered security architecture. The sequence in which you layer the controls together can depend on your use case.
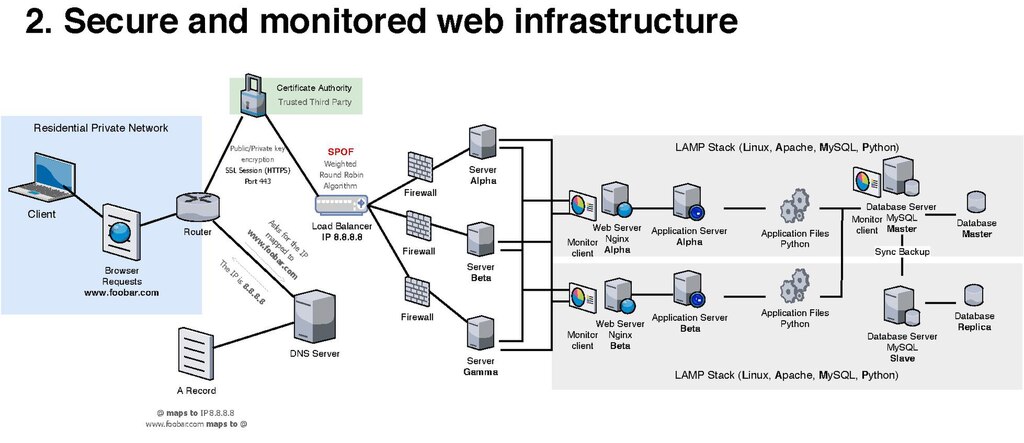
Recommended Network Architecture. When using deployment zones with more than one front-end server, you must use additional pieces of software (or hardware) to ensure that user requests get to the correct front-end servers where you deployed your OutSystems applications. You can use a load balancer to distribute load (according to a given ...
The Azure Architecture Center (AAC) helps you design, build, and operate solutions on Azure. Learn about the cloud architectural styles and design patterns. Use the technology choices and guides to decide the services that are right for your solution. The guidance is based on all aspects of building for the cloud, such as operations, security ...
The requested URL is not found · Click to go to Home
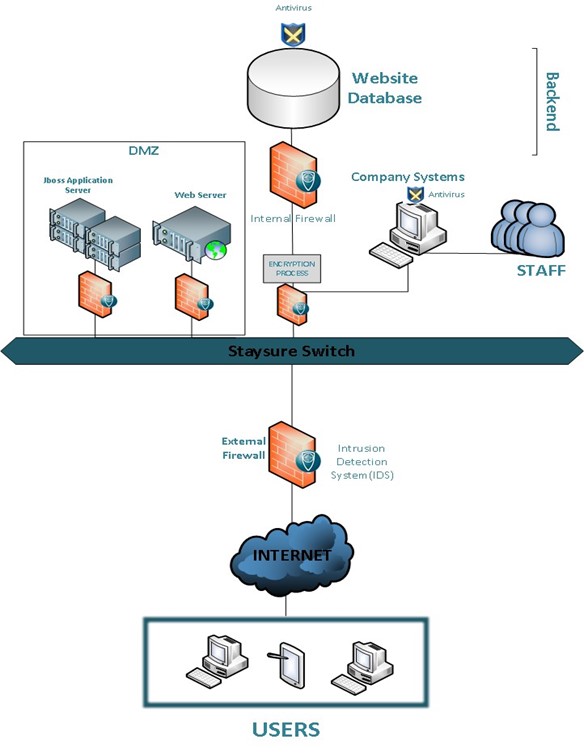
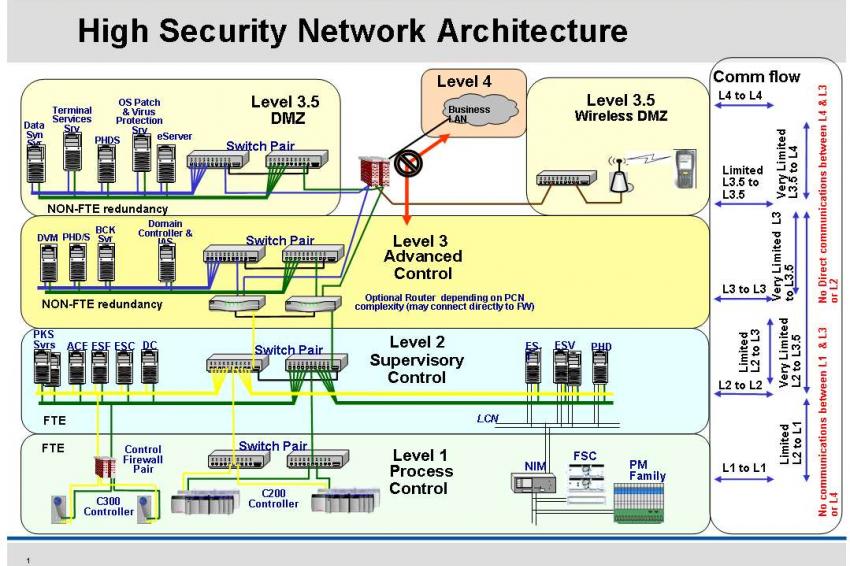
The diagram below represents the base-level ultra-secure network architecture, which meets all regulatory requirements and limits the likelihood of information being obtained as long as all of the architectural components are properly managed, maintained and monitored.
This site hold information on the recent advancements that are occurring in the world of Enterprise Architecture.
The Cybersecurity and Infrastructure Security Agency (CISA) issued on July 20, 2021, an alert (AA-22-2021A) addressing the successful Chinese intrusion of the United States oil and natural gas pipeline companies from 2011 to 2013. In its alert, CISA shares the frequency with which the attacks occurred, number of confirmed compromises, number of near misses, and the number of attacks whose depth of intrusion was undetermined. ## Chinese Fingers In The Infrastructure Pie. Attribution is an...
The client-server architecture or model has other systems connected over a network where resources are shared among the different computers. Typically, client server architecture is arranged in a way that clients are often situated at workstations or on personal computers, while servers are located elsewhere on the network, usually on more ...
Cloud Computing security architecture is categorized into frontend and backend, along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. Frontend, is a user/client-facing architecture. It comprises client-side interfaces and applications necessary to access Cloud Computing platforms.
Download scientific diagram | OPENFLOW NETWORK SECURITY ARCHITECTURE from ... Software-Defined Networking, Security and Data Center | ResearchGate, ...
Ran network architecture. The evolved packet core communicates with packet data networks in the outside world such as the internet private corporate networks or. Open radio access network RAN is a term for industry-wide standards for RAN interfaces that support interoperation between vendors equipment.
Network mapping tools can also be used to coordinate updates and act as documentation for external communication, onboarding, troubleshooting, etc. Use our network diagram maker to ensure that your network runs smoothly and is compliant with security standards like GDPR, PCI, and SOC 2.
The European Train Control System (ETCS) is the signalling and control component of the European Rail Traffic Management System (ERTMS). It is a replacement for legacy train protection systems and designed to replace the many incompatible safety systems currently used by European railways. The standard was also adopted outside Europe and is an option for worldwide application.
Hey all, pretty much like the post says. i got hurt last week (I dont want to get too nitty gritty on the details here to be safe but basically its my shoulder/bicep and i will be seeing a doctor tomorrow) and dont know if ill be out or just need modified duty, etc. Im nervous because I dont know what to expect. I know there are tons of injured techs/chronically injured techs working but I have done some reflection and I'm realizing that as much as I like being a tech, I think my body is giving ...
Microsoft announces Windows 365 Cloud PC at Inspire! [https://techcommunity.microsoft.com/.../initi.../m-p/2547471](https://techcommunity.microsoft.com/t5/windows-365/initial-isv-solutions-for-windows-365/m-p/2547471?fbclid=IwAR2OWXk0n2cjyj4HusL4HO8EFaqbErQD0fFPyjHlM11oDU58LCrjCyBhQW4) # Microsoft Windows 365: Introducing a New Product to End-user Computing >*On July 14th, 2021 at the annual Inspire conference, Microsoft announced a new service that holds the promise to establish Win...


![PDF] Construction of Network Security Architecture Based on ...](https://d3i71xaburhd42.cloudfront.net/0940af937eac9f9f90fbabe5193f672acc95c067/5-Figure4-1.png)










![PDF] The Global Voice of Information Security Network ...](https://d3i71xaburhd42.cloudfront.net/5756859705f57cfdf799fd2f790f5b7b0ccf334a/3-Figure2-1.png)






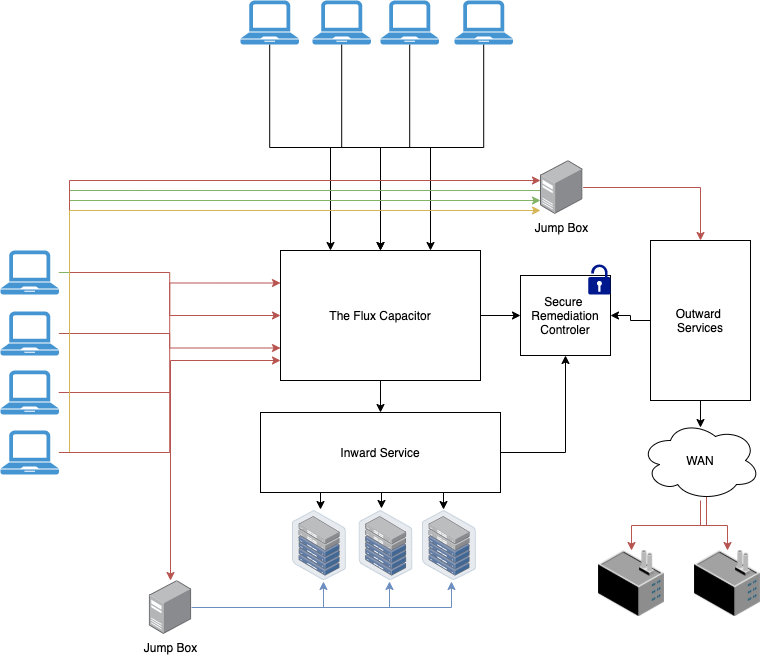


0 Response to "42 network security architecture diagram"
Post a Comment